Securing home network and computers for remote work

When we work as a remote developer, not having quick access to an IT/Security team makes our home networks and devices more at risk. That's why we must take extra steps to make things really secure. we need to make sure that personal and work-related information is safe, protecting against things like someone invading our privacy, stealing our identity, or causing financial harm. In this blog, we will talk about why it's important to keep our personal workspace safe and how we can make our home setups more secure, ensuring our remote work environment is safe and protected.
Why Prioritizing Security: Lessons from Past Data Breaches
- Home Router DNS Hijacking (2019): In 2019, there were reported cases of home routers being targeted for DNS hijacking attacks. Attackers manipulated router settings, redirecting users to malicious websites and potentially exposing sensitive personal information entered on these fraudulent sites.
- Mass Ransomware Attack (WannaCry 2017): In May 2017, the world witnessed a large-scale ransomware attack. Exploiting a vulnerability in Microsoft Windows systems, WannaCry rapidly spread across networks, encrypting files on infected computers. The attackers demanded ransom payments in Bitcoin for the decryption keys, impacting hundreds of thousands of computers globally. The attack not only affected individuals but also targeted businesses, healthcare systems, and government institutions.
- Social Engineering (2014 Yahoo Breach): In the 2014 Yahoo data breach, attackers gained access to Yahoo's internal systems through a combination of social engineering and spear-phishing. They targeted specific individuals, including high-level executives, to obtain login credentials and ultimately compromise a significant number of user accounts.
How you can be targeted?
Man-in-the-Middle (MITM) attack:

In this scenario, an attacker manipulates the Network protocols to redirect the network traffic through their device. This allows an attacker to intercept and potentially modify the data exchanged between the victim's device and the router. Now since the attacker can read and manipulate the data exchanged, it could lead to unauthorized access to our sensitive information such as login credentials or card details ultimately identity theft or unauthorized access to the victim's personal accounts.

Moreover, if an MITM attack succeeds, it allows harmful stuff to be added to the data flow, messing up the safety of the victim's device. This can lead to more problems by bringing in bad software. Once these bad programs get into our system, they can take full control of our personal devices and even affect other peripheral devices connected to our network like cameras and NAS (network-attached storage).
Phishing attacks: Let's dive into a prominent social engineering tactic, exemplified by phishing attacks. Phishing, a technique prevalent in the realm of remote work, involves attackers acting like trusted entities. They craft deceitful messages designed to appear secure and legitimate, attracting recipients to click on links, share login credentials, or download attachments. These fraudulent messages often refer to official communication from banks, organizations, or colleagues, posing a threat to the secure home networks of remote workers. When individuals interact with such deceptive content, attackers exploit the trust, compromising accounts, harvesting confidential data, and potentially delivering malware and having consequences similar to what we have seen in MITM attacks in the previous section.
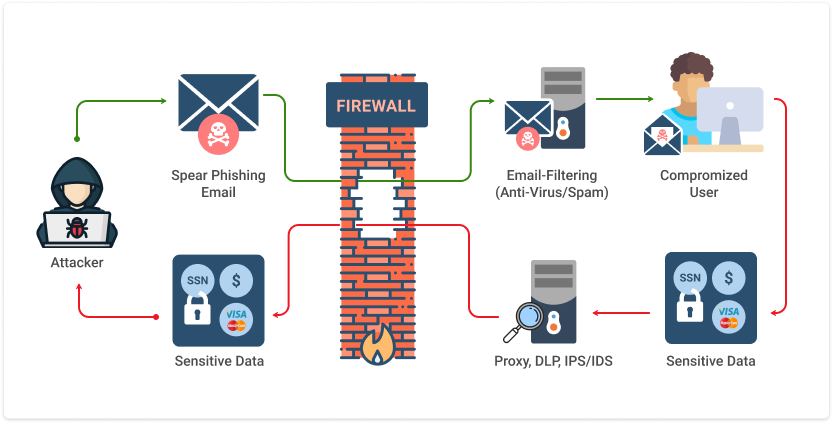
Remember, Bad actors are like silent watchers, waiting for any slip-ups. Stay savvy, stay safe! 🛡️.
A typical home network comprises a router, connecting devices like computers, smartphones, gaming consoles, and smart home devices. Additionally, network-attached storage, printers, streaming devices, and guest devices may also be part of the network.
Here are some security measures and checks we can implement to protect our home network:
Securing Home Router
Your router is a networking device that enables the communication between devices and connects them to the internet, serving as a central hub for data transmission in a local area network (LAN).
- Work-Personal Network Segmentation: To separate your work and personal networks on a home router, create distinct wireless networks or VLANs if supported. Additionally, establish a dedicated guest network for visitors to restrict their access solely to the primary network.
- Mac/IP Filtering: Mac filtering allows you to specify which devices are allowed to connect to your network based on their unique hardware addresses (MAC addresses). Similarly, IP filtering enables you to control access based on specific IP addresses. By configuring these filters, you can enhance network security by only permitting authorized devices to connect.
- Physical Locks and Enclosures: Unrestricted physical access to your router poses a serious security risk, enabling unauthorized individuals to tamper with network settings. Without protection on LAN internet access, vulnerabilities emerge, emphasizing the need for physical security measures like locked enclosures to safeguard against potential breaches and unauthorized access to your home network.
- Firewall Configuration: Configure the router's firewall settings to filter and control incoming and outgoing traffic. This adds an additional layer of protection by blocking potentially harmful traffic.
- Firmware Updates: Keep your router's firmware up to date. Regular updates from the manufacturer often include security patches, addressing vulnerabilities that could be exploited by attackers.
While some may be aware of these, several crucial aspects are often overlooked. These include employing the latest encryption standards like WPA2 or WPA3, establishing a robust password to safeguard against brute-force attacks, and changing the default gateway password to prevent unauthorized access to your router.
Safeguard your Personal Computer
In the digital age, it is essential to secure personal computers due to a range of potential threats. Cyber attackers employ various methods, including deploying malware through tactics like phishing or Man-in-the-Middle attacks, as discussed earlier. Therefore, safeguarding our personal computers is crucial.
Let's explore some common methods and techniques we can employ to ensure the security of our personal computers.
- Personal-Work System Segregation: Ensuring a dedicated computer for work is essential to protect sensitive data, it can also be achieved through a virtual machine (VM) or a distinct operating system on the same system. This approach significantly reduces the risk of potential security breaches by isolating work-related files and communications from personal activities, enhancing overall data security.
- Utilize encryption tools: Employ built-in encryption tools or third-party encryption software to encrypt sensitive files and folders, providing an extra layer of protection in case of loss or theft.
- Employ a VPN service: Enhance security, especially when accessing company resources, by using a VPN service to encrypt your internet connection, safeguarding your data and communications.
- Avoid third-party downloads: Refrain from downloading software or files from third-party websites, particularly those offering cracked versions or unofficial downloads, as they may host malware or compromised software.
- Use reputable antivirus software: Safeguard your computer from malicious software with regularly updated and reputable antivirus and anti-malware tools and Keep your system clean by performing routine scans for potential threats.
🌟 Think of antivirus software as your computer's bodyguard – always vigilant and ready to defend!
- Steer clear of public networks: Public networks can pose risks, inviting unauthorized individuals to connect and conduct potential Man-in-the-Middle (MITM) attacks, compromising your network traffic.
- Enable built-in firewall: Control incoming and outgoing network traffic by activating the built-in firewall on your computer to prevent unauthorized access.
- Backup and Recovery Plans: Regularly back up critical data and establish a robust data recovery plan. In the event of a cyber incident or data loss, having recent backups ensures minimal disruption and data recovery.
- Automatic screen locking and strong password: Enable automatic screen locking with a robust password and regularly update it as a precaution against unauthorized access when you are away from your computer. Utilize secure authentication methods like a PIN or fingerprint if supported.
Conclusion
In this article, we started with an examination of historical cybersecurity incidents, encompassing DNS hijacking of personal routers, ransomware, and social engineering attacks on individuals. The discussion emphasized the importance of adhering to secure practices to mitigate such threats. We then dive into prevalent attack vectors, including MITM and phishing attacks, describing their operational methods.
As a result, there could be problems like data breaches, unauthorized access, and messing with important information that belongs to your organization. Since it's your job to keep that data safe, if something goes wrong, it might impact how others see your professional reputation and your ability to protect sensitive information.
Subsequently, we discuss how to fortify home router security through measures like network segmentation, physical device security, and the implementation of Mac and IP filtering to protect ourselves from these threats. we also discuss securing personal computers, highlighting practices such as separating work and personal systems, employing encryption for storage security, and utilizing Virtual Private Networks (VPNs).
That was a summary of the discussion we had in community event last week, see you again this week for the next event on Discord.


![OS for Devs - Ubuntu vs nixOS vs macOS [Developers Roundtable]](/content/images/size/w750/2023/12/IMG_20231216_204048_584.jpg)



Member discussion