How developers can detect spy cameras to protect privacy IRL

Explained with the fundamentals of network communication and power
As software engineers, we're familiar with the digital/electronic systems and networks. This knowledge can be handy in detecting spy cameras to protect our privacy and security. In this article, we'll explore the technical aspects of spy cameras such as their communication methods, and power sources. We will then use those insights to plan specific steps to find spy cameras in the real world reliably and with the minimal cost possible.
Let's start with unpacking a spy camera to understand what's inside.
The anatomy of a spy camera

A spy camera has following components, usually packed in a deceiving compact case or a hole:
- Lens: Usually a pinhole or wide-angle lens for maximum coverage with minimal visibility
- Image Sensor: Typically a small CMOS sensor, similar to those found in smartphone cameras
- Microcontroller: A low-power MCU to capture image and transmit the data
- Power Source: Well, the electronics won't work without the power
- Storage: Often includes local storage (e.g., microSD card) for offline recording
- Communication Module: For transmitting data to a remote location
Network communication methods
While the spy cameras may store the data locally on a microSD card but that adds another logistical task for the attacker to get that card physically. Which can be defended relatively easily, specially when the premise is in your physical control.
But what if the video data is being transmitted in real-time?
In that case, spy cameras will typically need to use one of the following communication methods to transmit the video data:
- Wi-Fi: Most common in consumer-grade hidden cameras. They use standard 2.4GHz or 5GHz bands. This communication method will require another device within 100 feet to receive the data. This second device can either be used for monitoring or to further send the data to remote location via the internet.
- Cellular (3G/4G/5G): Used for remote monitoring. This method might be used if the logistics of setting up the second device in the near vicinity of the spy camera were not possible. But this approach might make the spy camera setup bulky and thus harder to hide.
- Bluetooth or Bluetooth Low Energy (BLE): Less common because the data transfer is limited up to 2Mbps. Which is not suitable for video streaming, specially if a high quality video is expected by the attacker. Also the data transmission range (~30 feet) is lower compared to WiFi. Having said that, it does have the benefits such as low power consumption and the compact size. So there are chances of this communication method being used.
- Custom Radio Frequency (RF): Older analog cameras will typically use this method. Custom RF with frequencies for larger range are typically not allowed by the law, and are continuously monitored by the law enforcement agencies for misuse. Typically it won't be a good choice by the attacker to use this method over WiFi (that is also RF but within the allowed bandwidth and with decent range). Having said that, if the attacker's goal is to extend the range a bit more than the WiFi while reducing the detectability, this method can be leveraged by them. But that will require powerful transmitter and high-gain antennas, making it a bulky setup or at least a complex setup involving multiple devices. This has been one of the favorite of law enforcement or intelligence agencies as it is harder to detect. If you have seen an old movie depecting a real-life scenerio where the detectives are sitting inside a VAN near to the home of the target, it will be a good guess that they used Custom Radio Frequency to get the data from the bug they planted in the home.
Ok, let's have a look at the comparison of these different communication methods at a glance.
| Method | Range | Power Consumption | Data Rate |
|---|---|---|---|
| Wi-Fi | 30-100m | Medium | Up to 600 Mbps |
| Cellular (3G/4G/5G) | Unlimited | High | 1-20 Mbps on 4G |
| Bluetooth | 10-100m | Low | 1-2 Mbps |
| Custom Radio Frequency (RF) | 30-100m | Medium | Low |
Note: Actual performance may vary depending on specific implementations and environmental factors.
Apart from these methods, theoretically there can be other methods as well but I doubt their practical usage in a real-life scenerio. So, we will skip their details but mention them briefly just for fun, the next Mission Impossible can get inspired from them:
- Power Line Communication (PLC) - range limited to throughout building's electrical system
- Li-Fi (Light Fidelity) - range limited to the line-of-sight
- Satellite - range unlimited (anywhere on the globe with clear sky) but requires a lot of money and power (electrical as well as the political)
Power sources
The power source often determines a spy camera's capabilities and placement:
- Battery-powered: Offers flexibility in placement but has limited operation time. Typical Lithium ION batteries (3000-6000 mAH) or AA cells will hardly provide the power for a single day operations. They will require additional logistics to recharge/replace the batteries. If you control/monitor the physical access reliably to the target premise, it will be easy for you to find/disable battery-powered cameras.
- Mains-powered: Provides continuous operation but requires proximity to an outlet. To find these cameras, all you need to do is to just look at all the power outlets and the possibility of hidden wiring.
- PoE (Power over Ethernet): Combines power and data transmission in a single cable. Look for the unidentified cables connected to your routers and make sure to secure your network. I hope you already have firewal enabled to not allow any device to connect if it does not have the mac address you identify to be yours.
- Solar-powered: For outdoor applications with extended operation time. I'm sure, it won't be hard to catch something that is powered by Solar, it will be big enough to be identified with the naked eyes.
Steps to detect the spy camera
Based on our understanding of spy camera components and its operation, we can make a list of steps to detect a spy camera. Starting from easy to hard techniques (for developers) to detect spy cameras:
1. Inspect visually

Start with the obvious one:
- Look for unusual objects or modifications in common hiding spots (smoke detectors, clocks, etc.).
- Check for unexplained holes or lens reflections.
- Use a flashlight to scan the room; camera lenses may reflect light.
2. Analyze network
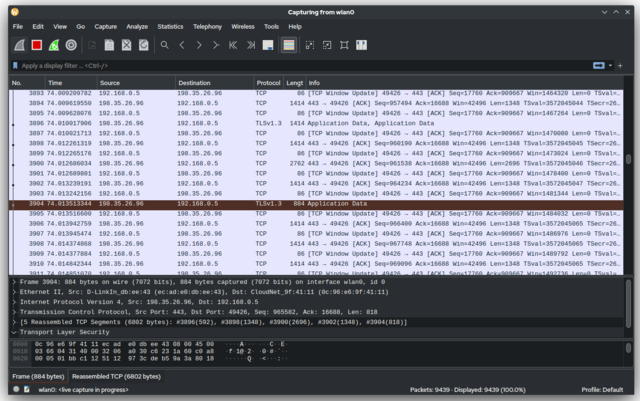
As software engineers, this is where our expertise shines. To rule out the spy cameras powered by ethernet (and connected to your network) or your own CCTV being hijacked, follow these steps:
- Check active connections to your WiFi router for unidentified devices
- Use tools like
Wiresharkornmapto scan for unfamiliar devices on the network - Monitor network traffic for patterns consistent with video streaming. Commonly used protocols for video streaming are RTSP, HLS, WebRTC, MJPEG, etc.
- Look for unexpected data streams or connections to unknown IP addresses
3. Use mobile apps
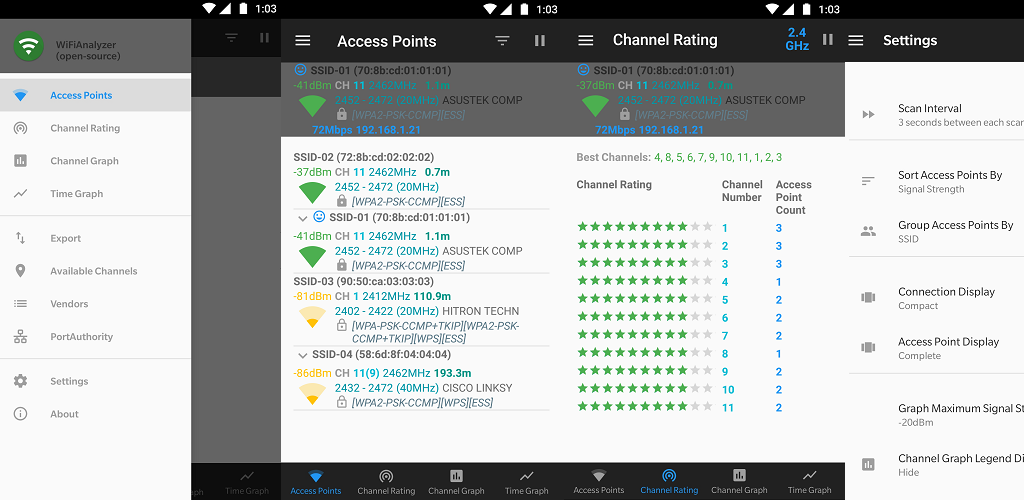
Your mobile is a computer as well as an RF antenna/receiver. It can be used in following ways to quickly identify if you have an unidentified data transmission:
- Use a Wi-Fi analyzer app to identify hidden networks or unusual devices
- Magnetic field detectors to find cameras with electromagnetic signatures
This one might not help as much as you want given the increasingly high density of Wi-Fi and electronic devices in your neighbourhood. But the clues from this step, combined with other techniques, can help you validate your suspicions.
4. Scan with an RF detector

RF scanner or detector are tools to measure the strength of radio frequencies. They will help you find the location of the source where the data is being transmitted from using RF. They can be as cheap as USD 50. Here's how you can use them:
- Scan for transmissions in the 1-6 GHz range (common for Wi-Fi and cellular)
- Pay attention to signal strength variations as you move around the space
5. Use thermal imaging
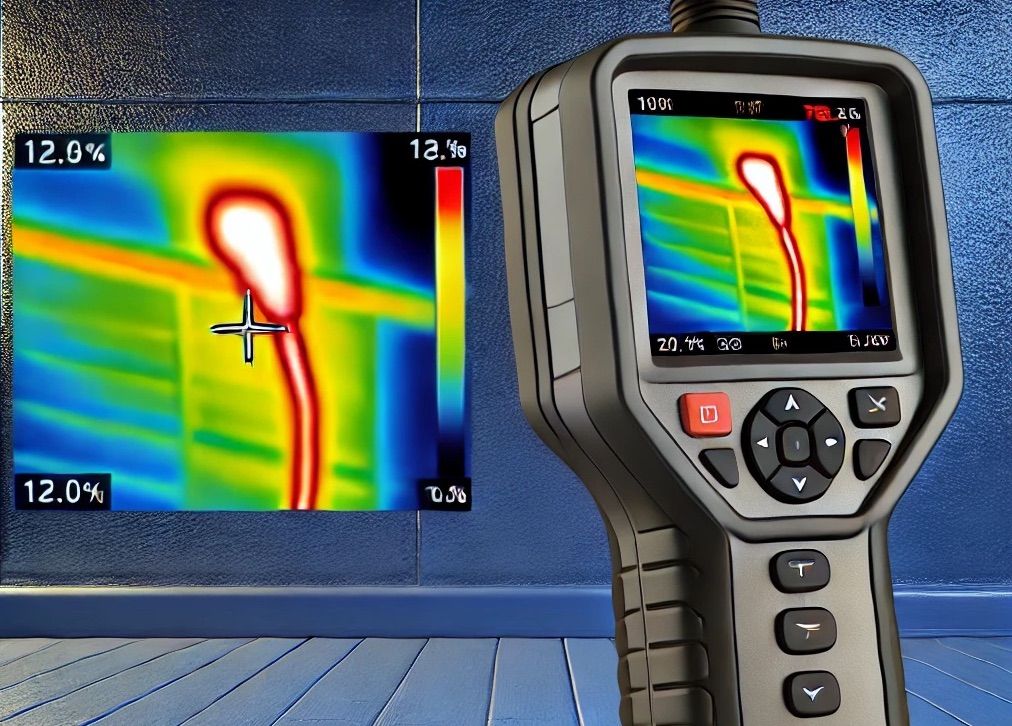
This can be used to find the hidden wiring or the camera in the physically inaccessible areas such as wall, pipes, etc. It is going to be expensive but nothing crazy (USD 200+) if you value privacy more.
- Use a thermal camera to detect heat signatures from active electronic devices
- Look for unexplained hot spots in walls, ceilings, or objects
Alternatively, you may choose to use an endoscopy camera if there's a possibility to pass a tiny wire inside those areas to look through but I'd advise to save your investment on endoscopy camera and just go with the thermal imaging, it will save you a lot of time and mental peace for some extra bucks.
6. Use an IR camera
If the spy camera is a night vision camera using. infrared LEDs, this step can help. You will need either an IR camera of your own or your smartphone camera can also work if it does not have an IR filter. Just turn off the lights and look through your IR camera to detect infrared LEDs used in the spy night vision cameras.
Conclusion
As software engineers, our understanding of networks and electronic systems gives us a unique advantage in detecting spy cameras. By combining this knowledge with the insights shared in this article, it should be easy to detect hidden cameras including the offline and live cameras.
Remember, the key is to think like both the attacker and the defender. If you've someone with you in accomplishing this task, I won't call you paranoid if one pretends to act as the attacker (the red team), and the other as a defender (the blue team). Use this knowledge responsibly to protect your privacy and make the world safer for everyone around you.



Member discussion